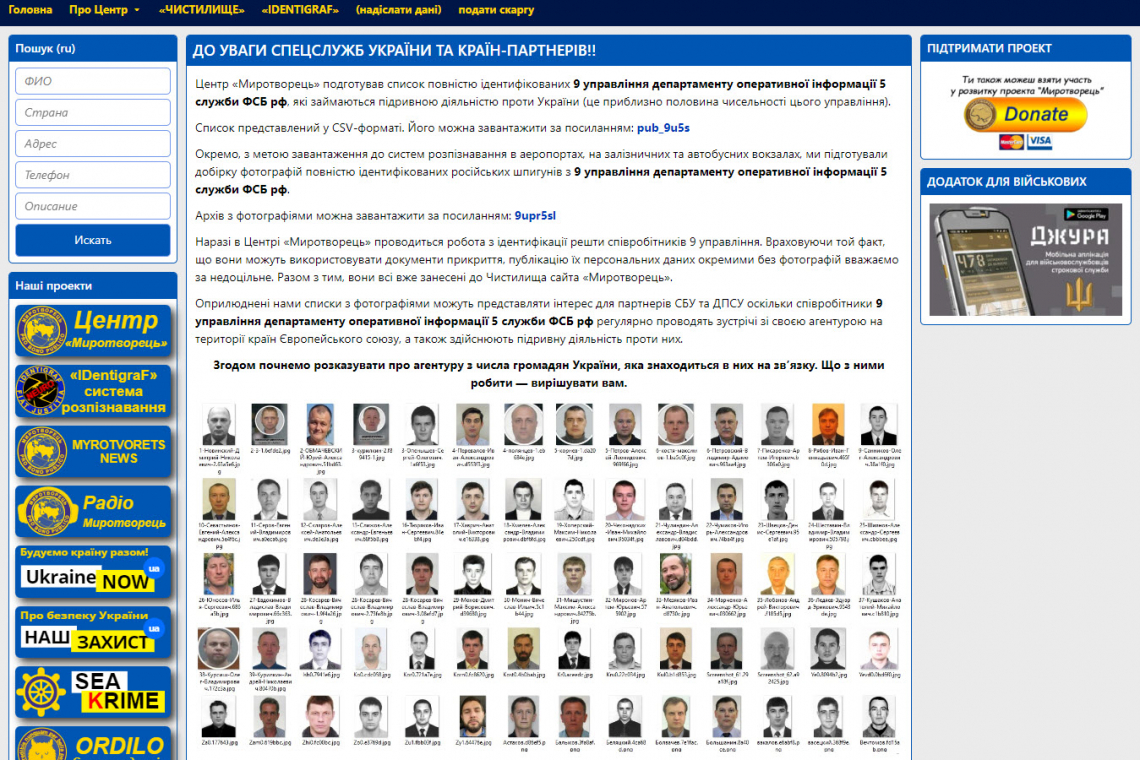
A web site that posts images and info of people OPPOSED to Ukraine in its fight with Russia, by strange coincidence seems to see some of the people whose photos and info they publish, GET KILLED. Now, we find, that web site . . . is hosted on (derives content from ) NATO servers!
Ok, so for those of you that can verify, I suggest the following:
Go to this Ukrainian website page, showing a composite image of many on the hit list: [link to myrotvorets.center (secure)]
If you examine the page source, depending on browser do something like = -> "Developer" -> "Page Source"
See that the image comes from here:
[link to psb4ukr.natocdn.net (secure)]
And the main image - with photos and names of people to "get" -- is also on NATO servers, HERE
Now, unix people can use a command called 'dig'.
Type:
dig natocdn.net
what comes back:
;; ANSWER SECTION:
natocdn.net. 300 IN A 152.152.31.120
So then we see whois this IP address, by typing the command 'whois':
whois 152.152.31.120
what comes back:
WOW
===
inetnum: 152.152.0.0 - 152.152.255.255
netname: NATO-HQ
org: ORG-NHQ1-RIPE
descr: NATO Headquarters
descr: Leopold III ln
descr: 1110 Brussels
country: BE
person: Eddy Vanderstraeten
address: NATO Headquarters
address: 1110 Brussels
address: BE
phone: +32 2 7075150
nic-hdl: EV431-RIPE
mnt-by: RIPE-ERX-MNT
created: 2004-02-02T14:54:06Z
last-modified: 2004-02-02T14:54:06Z
source: RIPE # Filtered